Use GPO to change the default behavior of potentially malicious file extensions.
If you’re like me and don’t have direct control of your own email filtering, or want to go a step beyond, you’re going to want a way to prevent non-PE viruses from running. Software Restriction Policies are good for this if you’re using them in a whitelist capacity, provided that you’ve also added the extension to the Designated File Types. From a blacklist standpoint it’s tougher.
Another way to approach the problem is to change the default program to open a particular file extension, and if nothing else it’s another layer of security. This has come up in response to .js-powered ransomware variants and, most recently, a .hta variant of Locky.
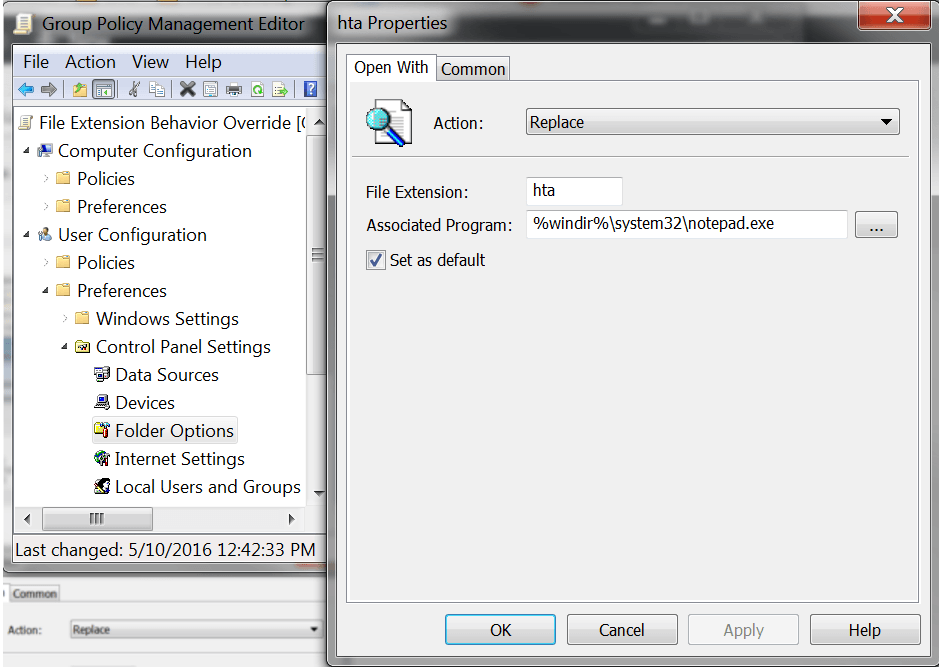
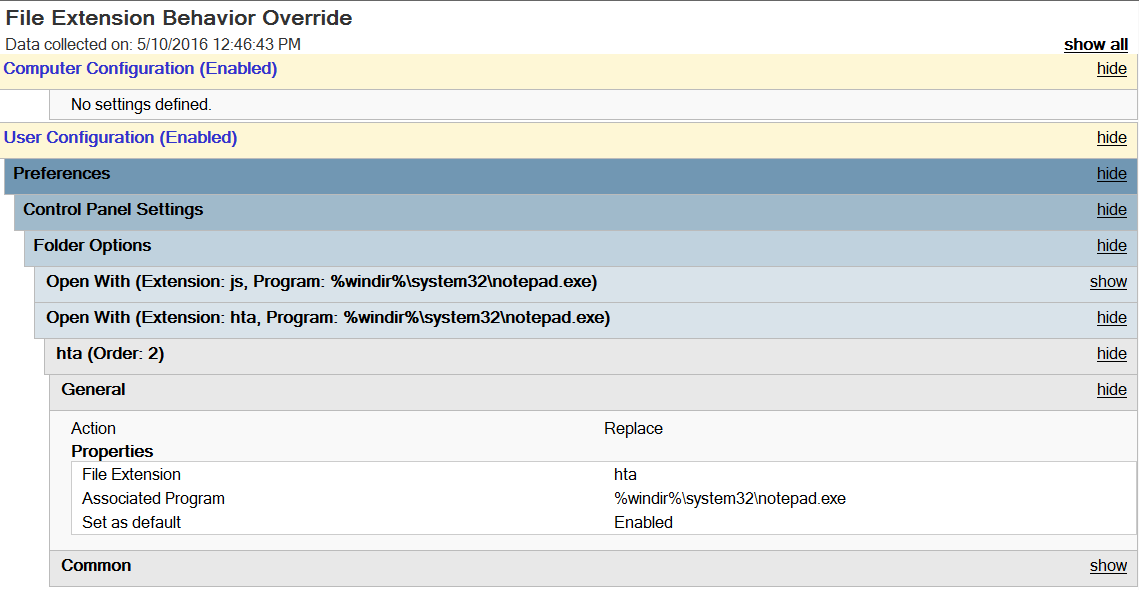
The policy is as follows:
User Configuration -> Preferences -> Control Panel Settings -> Folder Options -> Open With
Action: Replace File Extension: hta Associated Program: %windir%\system32\notepad.exe Set as default: Enabled.
These policies do require you to be either aware of any applications that this will impact or being willing to find out after it’s kicked in. Most organizations can modify .hta and .wsh with no negative repercussions. Many can modify .vbs but many cannot, as they are used by many old logon scripts still in use. Many can modify .js, as even those in web development are likely using an IDE to work with JavaScript files rather than simply double-clicking them. Just be aware of your environment’s needs when implementing this.
Enabling this policy and setting it to open in Notepad also benefits you because the end-user will still have something unusual (but now harmless) pop-up, a Notepad window that is full of dangerous-looking stuff. With any luck, they’ll notify the helpdesk so they can clean the system up.